Monday, December 22, 2008
some tricks to speed up Firefox
Done?
Good. Now, enter the URL about:config and then type in "network.http" to the browser's "filter" function to identify the following entries:
network.http.pipelining
network.http.proxy.pipelining
network.http.pipelining.maxrequests
If your Firefox is set up like mine, the first two will be set to "false". Change them to "true" and then enter a value like 20 for maxrequests.
These will make the browser use your network connection more efficiently (or, depending on your perspective, more aggressively) which should visibly speed up rendering pages in the browser.
There's a lot more you can learn if you pop over to Mozillazine's Firefox Tuning discussion, if you really want to fine-tune your Web browsing experience.
See these Websites to know more:
Firefox Keyboard shortcuts | Firefox Tutorial for Newbies
Finding IP address of sender in Yahoo, Gmail, Hotmail
Finding IP Address Of the Sender In Hotmail!!
- Click on Options on the top-right corner
- In the Mail Options page, click on Mail Display Settings
- In Message Headers, make sure Advanced option is checked.
- Click on Ok button
- Go back to the mails and open that mail.
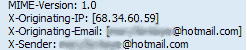
- Hotmail headers : Daniel ,In this case the IP address of the sender is [68.34.60.59]. This is be the IP address of the sender.

- Hotmail headers : Daniel
- Look for Received: from followed by IP address within square brackets[]. In this case, the IP address of the sender is [69.140.7.58].

- Hotmail headers : Daniel
- Look for Received: from followed by IP address within square brackets[].
In this case, the IP address of the sender is [61.83.145.129] .
Finding IP Address of the sender in Yahoo Mail!!
- Click on Options on the top-right corner
- In the Mail Options page, click on General Preferences
- Scroll down to Messages where you have the Headers option
- Make sure that Show all headers on incoming messages is selected
- Click on the Save button
- Go back to the mails and open that mail.
- Yahoo! headers : Daniel.

Finding IP Address of the sender in Gmail !!
When you receive an email, you receive more than just the message. The email comes with headers that carry important information that can tell where the email was sent from and possibly who sent it. For that, you would need to find the IP address of the sender. The tutorial below can help you find the IP address of the sender.- Log into your Gmail account with your username and password.
- Open the mail.
- To display the headers,
- Click on More options corresponding to that thread. You should get a bunch of links. Click on Show original
- You should get headers like this:
- Gmail headers : Daniel

- Look for Received: from followed by a few hostnames and an IP address between square brackets. In this case, it is 69.138.30.1
- That is be the IP address of the sender!!
How to create a password reset disk for XP?
*To create a password reset disk:
1) Insert a blank floppy disk into drive.
2) Open User Accounts in Control Panel.
3) Double-click on your account name.
4) On the left side of the window, under Related Tasks, select Prevent a forgotten password. A wizard will pop up and walk you through the process of creating the password recovery disk. If the related tasks does not show up you are not double clicking on the user account or you are using a LAN with domains.
*If your computer is on a domain, you can create the Domain Password Reset Disk as follows.
1) Press CTRL+ALT+DELETE to open the Windows Security dialog box.
2) Click Change Password.
3) In the "Log on to" click on the down arrow to select local XP machine.
4) Click Backup to open the Forgotten Password Wizard. If you don't see the Backup button you did not select the computer in step 3 correctly.
5) Click Next and then follow the instructions as they appear on the screen.
You will be prompted to create a new password. Remember, anyone who has the password reset disk can access the system, so don't forget to store your disk in a safe place!
Tuesday, August 5, 2008
FASTEST WAY TO HACK INTO **** SYSTEM
steps: -
1.Download software PORT SCANNER.
2.Copy the ip address of the victim whose port is open.
3.Download NETLAB which gives u all information includes victim ip address,Area from where he is accessing internet....
4.Paste the ip of victim u found initially into NETLAB .Thats it u access his system.
NetLab 1.4 Free Download!!!
Friday, August 1, 2008
How to Hack Into a Windows XP Computer Without Changing Password

How to Hack Into a Windows XP Computer Without Changing Password -
Steps to Hack into a Windows XP Computer without changing password:
1. Get physical access to the machine. Remember that it must have a CD or DVD drive.
2. Download DreamPackPL HERE.
3. Unzip the downloaded dpl.zip and you’ll get dpl.ISO.
4. Use any burning program that can burn ISO images.
5. After you have the disk, boot from the CD or DVD drive. You will see Windows 2000 Setup and it will load some files.
6. Press “R” to install DreamPackPL.
7. Press “C” to install DreamPackPL by using the recovery console.
8. Select the Windows installation that is currently on the computer (Normally is “1″ if you only have one Windows installed)
9. Backup your original sfcfiles.dll by typing:
“ren C:\Windows\System32\sfcfiles.dll sfcfiles.lld” (without quotes)
10. Copy the hacked file from CD to system32 folder. Type:
“copy D:\i386\pinball.ex_ C:\Windows\System32\sfcfiles.dll” (without quotes and assuming your CD drive is D:)
11. Type “exit”, take out disk and reboot.
12. In the password field, type “dreamon” (without quotes) and DreamPack menu will appear.
13. Click the top graphic on the DreamPack menu and you will get a menu popup.
How to Hack Into a Windows XP Computer Without Changing Password

14. Go to commands and enable the options and enable the god command.
How to Hack Into a Windows XP Computer Without Changing Password

15. Type "god" in the password field to get in Windows.
You can also go to Passwords and select "Logon with wrong password and hash". This option allows you to login with ANY password.
Note: I was unable to bring up the DreamPackPL for the first time because I have Kaspersky Anti-Virus already running in background. I believe most antivirus already labelled this tool as a Hack-Tool. A Hack-Tool is NOT a virus. DreamPackPL helps you bypass the Windows Login screen and it is not destructive.
Msn password cracking
Hacking MSN is actually VERY simple. Msn is designed to route the connection through a Microsoft server while you are chatting. However, when a file is sent, a DCC (direct connection) is created. This was purposely done because otherwise Microsoft would waste a lot of bandwidth so a direct connection is made. This is your chance. Make a file transfer occur between u and a victim (try to send a big file), open up your command prompt (run "cmd" in NT/XP or "command" in 9X to get into prompt) and run netstat. usually the MSN targets IP would be above port 2000. enjoy.
If u receive some crap like gux1-43.primus.com as the target, do a reverse DNS lookup on it. However, this occurs very rarely, mostly u will receive a clear IP.
once u have d IP u can do anything with him by Fingerprinting.
U can protect yourself from this occurring to you by using a proxy with MSN (under connections panel in options).
close Welcome! Wikis are websites that everyone can build together. It's easy! Crack Yahoo,Hotmail,Msn password
**Here m going to reveal n Alert About how the Unethical Hackers Can cheat us .
This Page is meant for Educational Purpose only.
I do not Endorse Hacking at all
but its Meant for knowing the Threats n Protect yourself also Curbing them**
Here we present:
1:- How hotmail can be hacked with fake login screen (2 different ways)
2:- Fake e-mails threats
3:- Detect a fake message into hotmail
4:- How to get persons ip address through msn messenger
5:- curbing the way hackers get the passwords
6:- Easiest Way
7:- Change msn messenger title
8:- Protect yourself from Virus
9:- Hoax Toolbox v1.1
1) Protect yourself from Phishing
Usually The Unethical Hackers Upload their hotmail's fake login screen on a web server and then send these codes
to the victim from yahoo or another mail sending program. The codes are
and the user will be automatically redirected to your fake hotmail screen from their e-mail
box & you r Hacked.
Beware of There Threats
2) Beware of Fake Login Screens
They Start chatting with your victim and send him the fake login screen through Their messenger and try to pish you.
there are many many of them available on the net.. which are usually small Visual Basic programs.. never reveal your password anywhere other than the latest Versions of msn Messengers.
2:- Fake e-mails threats
This is very easy go to http://www.boxfrog.com/ register( its blocked now) but there are many others .. google u ll find many
click on create message and in from filed type in any ones e-mail address and the message will
be sent.
there's also a simple way of doing this by Telnet ting from the dos Prompt..
Beware of this Threat .. make your spam protection Powerful
3) Detect a fake message into Hotmail inbox.
This is Simple Buddies.. open your e-mail box go to options select display setting or
message display setting or (some thing like this) now select full where it says message display
settings or something like this. Open the mail which u thought to be fake now in the last
where it says from u can see the address of that site from where the mail is sent but if
some one has sent it through some sort of program it will tell u his ip.
n once you know D ip m sure u know how to go between it there after
IMP: Read the ip address log from Backwards..
4)- Protect urself revealing your ip address through msn messenger.
When you Open your messenger start chatting with friend open ms dos and type netstat -n there
do not press enter and then minimize it after this send something to your victim and as soon as he accept it the hotmail messenger will say connecting this is the time when u re maximize your MS-DOS and
press enter the ip address next to time wait: will the friends ip. U may be Hacked The same way
Beware!!
HoaX Toolbox v1.1
This is a PHP script that creates a website with an admin area that allows the user to choose between fake login pages of MSN Messenger, Hotmail, Yahoo and Google Mail, once you set up the script on a server that has PHP and SQL you will be able to log in the administration page and choose the fake login page to display to the main site, when the victim tries to log-in their mail/messenger, the website keeps the user/pass information in a log file that you can view anytime from the admin area, if the victim is not stupid enough to add their real log-in because they read the URL of your server instead of reading hotmail.com or yahoo.com in the URL bar then remember you can pop-up the main page of the site and disable the URL bar on the explorer, so when the user clicks on your real site the link "Yahoo Mail" an explorer without URL bar pops up, if you don't know how to pop up customized browsers search google
Key logging
SAIMOHAN
Hack a Yahoo Account While Chatting
So who ever try this is at his risk.
I am not sure that this will work 100 %.
But yes will work almost 70 percent of the times.
But before that you need to know some few things of yahoo chat protocol
leave a comment here after u see the post lemme know if it does works or not or u having a problem post here.
Following are the features : -
1) When we chat on yahoo every thing goes through the server.Only when we chat thats messages.
2) When we send files yahoo has 2 options
a) Either it uploads the file and then the other client has to down load it.
Either it connects to the client directly and gets the files
3) When we use video or audio:-
a) It either goes thru the server
Or it has client to client connection
And when we have client to client connection the opponents IP is revealed.On the 5051 port.So how do we exploit the Chat user when he gets a direct connection. And how do we go about it.Remember i am here to hack a system with out using a TOOL only by simple net commands and yahoo chat techniques.Thats what makes a difference between a real hacker and new bies.
So lets analyse
1) Its impossible to get a Attackers IP address when you only chat.
2) There are 50 % chances of getting a IP address when you send files
3) Again 50 % chances of getting IP when you use video or audio.
So why to wait lets exploit those 50 % chances .
I'll explain only for files here which lies same for Video or audio
1) Go to dos
type ->
netstat -n 3
You will get the following output.Just do not care and be cool
Active Connections
Proto Local Address Foreign Address State
TCP 194.30.209.15:1631 194.30.209.20:5900 ESTABLISHED
TCP 194.30.209.15:2736 216.136.224.214:5050 ESTABLISHED
TCP 194.30.209.15:2750 64.4.13.85:1863 ESTABLISHED
TCP 194.30.209.15:2864 64.4.12.200:1863 ESTABLISHED
Active Connections
Proto Local Address Foreign Address State
TCP 194.30.209.15:1631 194.30.209.20:5900 ESTABLISHED
TCP 194.30.209.15:2736 216.136.224.214:5050 ESTABLISHED
TCP 194.30.209.15:2750 64.4.13.85:1863 ESTABLISHED
TCP 194.30.209.15:2864 64.4.12.200:1863 ESTABLISHED
Just i will explain what the out put is in general.In left hand side is your IP address.And in right hand side is the IP address of the foreign machine.And the port to which is connected.Ok now so what next ->
2) Try sending a file to the Target .
if the files comes from server.Thats the file is uploaded leave itYou will not get the ip.But if a direct connection is established
HMMMM then the first attacker first phase is over
This is the output in your netstat.The 5101 number port is where the Attacker is connected.
Active Connections
Proto Local Address Foreign Address State
TCP 194.30.209.15:1631 194.30.209.20:5900 ESTABLISHED
TCP 194.30.209.15:2736 216.136.224.214:5050 ESTABLISHED
TCP 194.30.209.15:2750 64.4.13.85:1863 ESTABLISHED
TCP 194.30.209.15:2864 64.4.12.200:1863 ESTABLISHED
TCP 194.30.209.15:5101 194.30.209.14:3290 ESTABLISHED
3) so what next???
Hmmm........ Ok so make a DOS attack now
Go to dos prompt and
Just do
nbtstat -A Attackers IPaddress.Can happen that if system is not protected then you can see the whole network.
C:\>nbtstat -A 194.30.209.14
Local Area Connection:
Node IpAddress: [194.30.209.15] Scope Id: []
NetBIOS Remote Machine Name Table
Name Type Status
---------------------------------------------
EDP12 <00> UNIQUE Registered
XYZ <00> GROUP Registered
XYZ <20> UNIQUE Registered
XYZCOMP1 <1e> GROUP Registered
MAC Address = 00-C0-W0-D5-EF-9A
Ok so you will ask now what next???
No you find what you can do with this network than me explaining everything.
so post ur comments and lemme know....
So the conclusion is never exchange files , video or audio till you know that the user with whom you are chatting is not going to harm you
How To Become A Hacker
Hackers solve problems and build things, and they believe in freedom and voluntary mutual help. To be accepted as a hacker, you have to behave as though you have this kind of attitude yourself. And to behave as though you have the attitude, you have to really believe the attitude.
But if you think of cultivating hacker attitudes as just a way to gain acceptance in the culture, you'll miss the point. Becoming the kind of person who believes these things is important for you -- for helping you learn and keeping you motivated. As with all creative arts, the most effective way to become a master is to imitate the mind-set of masters -- not just intellectually but emotionally as well. So, if you want to be a hacker, repeat the following things until you believe them:
1. The world is full of fascinating problems waiting to be solved.
Being a hacker is lots of fun, but it's a kind of fun that takes lots of effort. The effort takes motivation. Successful athletes get their motivation from a kind of physical delight in making their bodies perform, in pushing themselves past their own physical limits. Similarly, to be a hacker you have to get a basic thrill from solving problems, sharpening your skills, and exercising your intelligence.If you aren't the kind of person that feels this way naturally, you'll need to become one in order to make it as a hacker. Otherwise you'll find your hacking energy is sapped by distractions like sex, money, and social approval. (You also have to develop a kind of faith in your own learning capacity -- a belief that even though you may not know all of what you need to solve a problem, if you tackle just a piece of it and learn from that, you'll learn enough to solve the next piece -- and so on, until you're done.)
2. Nobody should ever have to solve a problem twice.
Creative brains are a valuable, limited resource. They shouldn't be wasted on re-inventing the wheel when there are so many fascinating new problems waiting out there.To behave like a hacker, you have to believe that the thinking time of other hackers is precious -- so much so that it's almost a moral duty for you to share information, solve problems and then give the solutions away just so other hackers can solve new problems instead of having to perpetually re-address old ones. (You don't have to believe that you're obligated to give all your creative product away, though the hackers that do are the ones that get most respect from other hackers. It's consistent with hacker values to sell enough of it to keep you in food and rent and computers. It's consistent to use your hacking skills to support a family or even get rich, as long as you don't forget you're a hacker while you're doing it.)
3. Boredom and drudgery are evil.
Hackers (and creative people in general) should never be bored or have to drudge at stupid repetitive work, because when this happens it means they aren't doing what only they can do -- solve new problems. This wastefulness hurts everybody. Therefore boredom and drudgery are not just unpleasant but actually evil.To behave like a hacker, you have to believe this enough to want to automate away the boring bits as much as possible, not just for yourself but for everybody else (especially other hackers). (There is one apparent exception to this. Hackers will sometimes do things that may seem repetitive or boring to an observer as a mind-clearing excercise, or in order to acquire a skill or have some particular kind of experience you can't have otherwise. But this is by choice -- nobody who can think should ever be forced into boredom.)
4. Freedom is good.
Hackers are naturally anti-authoritarian. Anyone who can give you orders can stop you from solving whatever problem you're being fascinated by -- and, given the way authoritarian minds work, will generally find some appallingly stupid reason to do so. So the authoritarian attitude has to be fought wherever you find it, lest it smother you and other hackers.(This isn't the same as fighting all authority. Children need to be guided and criminals restrained. A hacker may agree to accept some kinds of authority in order to get something he wants more than the time he spends following orders. But that's a limited, conscious bargain; the kind of personal surrender authoritarians want is not on offer.) Authoritarians thrive on censorship and secrecy. And they distrust voluntary cooperation and information-sharing -- they only like `cooperation' that they control. So to behave like a hacker, you have to develop an instinctive hostility to censorship, secrecy, and the use of force or deception to compel responsible adults. And you have to be willing to act on that belief.
5. Attitude is no substitute for competence.
To be a hacker, you have to develop some of these attitudes. But copping an attitude alone won't make you a hacker, any more than it will make you a champion athlete or a rock star. Becoming a hacker will take intelligence, practice, dedication, and hard work.Therefore, you have to learn to distrust attitude and respect competence of every kind. Hackers won't let posers waste their time, but they worship competence -- especially competence at hacking, but competence at anything is good. Competence at demanding skills that few can master is especially good, and competence at demanding skills that involve mental acuteness, craft, and concentration is best. If you revere competence, you'll enjoy developing it in yourself -- the hard work and dedication will become a kind of intense play rather than drudgery. And that's vital to becoming a hacker. Basic Hacking Skills The hacker attitude is vital, but skills are even more vital. Attitude is no substitute for competence, and there's a certain basic toolkit of skills which you have to have before any hacker will dream of calling you one.
This tookit changes slowly over time as technology creates new skills and makes old ones obsolete. For example, it used to include programming in machine language, and didn't until recently involve HTML. But in late 1996 it pretty clearly includes the following:
1. Learn how to program.
This, of course, is the fundamental hacking skill. In 1997 the one language you absolutely must learn is C (though it's not the one to try learning first thing). But you aren't a hacker or even merely a programmer if you only know one language -- you need to learn how to think about programming problems in a general way, independent of any one language. To be a real hacker, you need to have gotten to the point where you can learn a new language in days by relating what's in the manual to what you already know. This means you should learn several very different languages.Besides C, you should also learn at least LISP and Perl (and Java is pushing hard for a place on the list). Besides being the most important hacking languages, these each represent very different approaches to programming, and all will educate you in valuable ways. I can't give complete instructions on how to learn to program here -- it's a complex skill. But I can tell you that books and courses won't do it (many, maybe most of the best hackers are self-taught). What will do it is (a) reading code and (b) writing code. Learning to program is like learning to write good natural language. The best way to do it is to read some stuff written by masters of the form, write some things yourself, read a lot more, write a little more, read a lot more, write some more ... and repeat until your writing begins to develop the kind of strength and economy you see in your models. Finding good code to read used to be hard, because there were few large programs available in source for fledgeling hackers to read and tinker with. This has changed dramatically; free software, free programming tools, and free operating systems (all available in source, and all built by hackers) are now widely available. Which brings me neatly to our next topic...
2. Get one of the free UNIXes and learn to use and run it.
I'm assuming you have a personal computer or can get access to one (these kids today have it so easy :-)). The single most important step any newbie can take towards acquiring hacker skills is to get a copy of Linux or one of the free BSD-Unixes, install it on a personal machine, and run it.Yes, there are other operating systems in the world besides Unix. But they're distributed in binary -- you can't read the code, and you can't modify it. Trying to learn to hack on a DOS or Windows machine or under MacOS is like trying to learn to dance while wearing a body cast. Besides, Unix is the operating system of the Internet. While you can learn to use the Internet without knowing Unix, you can't be an Internet hacker without understanding it. For this reason, the hacker culture today is pretty strongly Unix-centered. (This wasn't always true, and some old-time hackers aren't happy about it, but the symbiosis between Unix and the Internet has become strong enough that even Microsoft's muscle doesn't seem able to seriously dent it.) So, bring up a Unix -- I like Linux myself but there are other ways. Learn it. Run it. Tinker with it. Talk to the Internet with it. Read the code. Modify the code. You'll get better programming tools (including C, Lisp, and Perl) than any Microsoft operating system can dream of, you'll have fun, and you'll soak up more knowledge than you realize you're learning until you look back on it as a master hacker.
3. Learn how to use the World Wide Web and write HTML.
Most of the things the hacker culture has built do their work out of sight, helping run factories and offices and universities without any obvious impact on how non-hackers live. The Web is the one big exception, the huge shiny hacker toy that even politicians admit is changing the world. For this reason alone (and a lot of other good ones as well) you need to learn how to work the Web.This doesn't just mean learning how to drive a browser (anyone can do that), but learning how to write HTML, the Web's markup language. If you don't know how to program, writing HTML will teach you some mental habits that will help you learn. So build a home page. But just having a home page isn't anywhere near good enough to make you a hacker. The Web is full of home pages. Most of them are pointless, zero-content sludge -- very snazzy-looking sludge, mind you, but sludge all the same .
Status in the Hacker Culture Like most cultures without a money economy, hackerdom runs on reputation. You're trying to solve interesting problems, but how interesting they are, and whether your solutions are really good, is something that only your technical peers or superiors are normally equipped to judge.
Accordingly, when you play the hacker game, you learn to keep score primarily by what other hackers think of your skill (this is why you aren't really a hacker until other hackers consistently call you one). This fact is obscured by the image of hacking as solitary work; also by a hacker-cultural taboo (now gradually decaying but still potent) against admitting that ego or external validation are involved in one's motivation at all. Specifically, hackerdom is what anthropologists call a gift culture. You gain status and reputation in it not by dominating other people, nor by being beautiful, nor by having things other people want, but rather by giving things away. Specifically, by giving away your time, your creativity, and the results of your skill. There are basically five kinds of things you can do to be respected by hackers:
1. Write free software.
The first (the most central and most traditional) is to write programs that other hackers think are fun or useful, and give the program sources to the whole hacker culture to use.Hackerdom's most revered demigods are people who have written large, capable programs that met a widespread need and given them away, so that now everyone uses them.
2. Help test and debug free software
They also serve who stand and debug free software. In this imperfect world, we will inevitably spend most of our software development time in the debugging phase. That's why any free-software author who's thinking will tell you that good beta-testers (who know how to describe symptoms clearly, localize problems well, can tolerate bugs in a quickie release, and are willing to apply a few simple diagnostic routines) are worth their weight in rubies. Even one of these can make the difference between a debugging phase that's a protracted, exhausting nightmare and one that's merely a salutory nuisance.If you're a newbie, try to find a program under development that you're interested in and be a good beta-tester. There's a natural progression from helping test programs to helping debug them to helping modify them. You'll learn a lot this way, and generate good karma with people who will help you later on.
3. Publish useful information.
Another good thing is to collect and filter useful and interesting information into Web pages or documents like FAQs (Frequently Asked Questions lists), and make those generally available.Maintainers of major technical FAQs get almost as much respect as free-software authors.
4. Help keep the infrastructure working.
The hacker culture (and the engineering development of the Internet, for that matter) is run by volunteers. There's a lot of necessary but unglamorous work that needs done to keep it going -- administering mailing lists, moderating newsgroups, maintaining large software archive sites, developing RFCs and other technical standards.People who do this sort of thing well get a lot of respect, because everybody knows these jobs are huge time sinks and not much fun as playing with code. Doing them shows dedication.
Q: What language should I learn first?
HTML, if you don't already know it. There are a lot of glossy, hype-intensive bad HTML books out there, and distressingly few good ones. The one I like best is HTML: The Definitive Guide.When you're ready to start programming, I would recommend starting with Perl or Python. C is really important, but it's also much harder.
Q: How can I get started? Where can I get a free Unix?
Elsewhere on this page I include pointers to where to get a Linux. To be a hacker you need motivation and initiative and the ability to educate yourself. Start now...make Your windows original
OR http://wannabegeek.org/component/option,com_docman/task,doc_download/gid,27/Itemid,120/
Extract the archive to retrieve the registration file.
Double click on the registry entry file (with .reg extension), and answer Yes when asked whether want to add the information to the registry to hack the registry.
The Windows is fully licensed, legal, genuine and activated. You should be able to pass all validation of Windows Genuine Advantage program required at anywhere, including Windows Update or Microsoft Update, Microsoft Download Center, validate with Microsoft Genuine Advantage Diagnostic Tool, validate from Genuine Microsoft Windows online, setup installation of WGA apps and etc. Of course, until the next Microsoft update.
The registration file actually put in the following registry keys and branches to the Windows registry:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\WPAEvents]
“OOBETimer”=hex:ff,d5,71,d6,8b,6a,8d,6f,d5,33,93,fd
“LastWPAEventLogged”=hex:d5,07,05,00,06,00,07,00,0f,00,38,00,24,00,fd,02
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion]
“CurrentBuild”=”1.511.1 () (Obsolete data - do not use)”
“InstallDate”=dword:427cdd95
“ProductId”=”69831-640-1780577-45389″
“DigitalProductId”=hex:a4,00,00,00,03,00,00,00,36,39,38,33,31,2d,36,34,30,2d,\
31,37,38,30,35,37,37,2d,34,35,33,38,39,00,5a,00,00,00,41,32,32,2d,30,30,30,\
30,31,00,00,00,00,00,00,00,00,0d,04,89,b2,15,1b,c4,ee,62,4f,e6,64,6f,01,00,\
00,00,00,00,27,ed,85,43,a2,20,01,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,31,34,35,30,34,00,00,00,00,00,00,00,ce,0e,\
00,00,12,42,15,a0,00,08,00,00,87,01,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,94,a2,b3,ac
“LicenseInfo”=hex:9e,bf,09,d0,3a,76,a5,27,bb,f2,da,88,58,ce,58,e9,05,6b,0b,82,\
c3,74,ab,42,0d,fb,ee,c3,ea,57,d0,9d,67,a5,3d,6e,42,0d,60,c0,1a,70,24,46,16,\
0a,0a,ce,0d,b8,27,4a,46,53,f3,17
If you can’t download the files above, simply open any text editor, copy and paste the above text (make sure the format is text only and not a rich text, as the quotation marks (which is distorted by WordPress) matter to make the registration file you created yourself works), and the save the file with .reg extension. The double click on the .reg you created to apply the registry trick.
VoIP Hacks
|
Calls made over VoIP travel over the Internet, as do any other Internet packets. They are then transferred to the normal phone system via a gateway so that you can call any phone in the world as you would with any telephone. You receive calls in the same way. Someone makes a call on a normal telephone, and that call travels over the normal telephone system, then is sent to a gateway where the call is broken into IP packets and delivered over the Internet to your telephone. With this type of VoIP service, you get your own phone number, just like any phone number. In fact, you might even be able to keep your existing phone number. There are also software-only VoIP services, in which you don't use any special hardware or equipment. Instead, you download a piece of software and use your PC's speakers and microphone to talk, or else plug a headset into your PC's microphone jack. Generally, these only let you call others who use the same software that you do; in other words, you can't make calls to normal telephones, but can make them to those who also use the same VoIP software you're using. In this scenario, the phone call travels over the Internet. It never actually travels to the normal phone system because the calls aren't made to normal telephones. These VoIP services are typically free. They don't offer full service plans, and so don't have caller ID, call waiting, and similar features. In fact, instant messenger programs such as AOL Instant Messenger, Yahoo! Messenger, and Windows Messenger let you make calls this way. Some of these services let you make phone calls to regular telephones as well, although for that they charge you a fee. And for now, anyway, you can't receive normal phone calls on them; you can make phone calls only. But that is expected to change. The best-known full-featured VoIP service that lets you make phone calls to anyone and receive phone calls is Vonage (http://www.vonage.com). It offers a variety of service plansfor example, $14.99 per month for 500 minutes of calls per month to anywhere in the U.S or Canada, or $24.99 per month for unlimited calls per month to anywhere in the U.S. or Canada. All plans include a variety of free services, such as voicemail, caller ID, call waiting, call forwarding, call transfer, and three-way calling. And international calls are as low as 2 cents per minute to London, Paris, Rome, and Hong Kong. A variety of other companies are entering the VoIP market, including ISPs and AT&T. The best-known software-only VoIP service is Skype (http://www.skype.com), which is available for free when you make calls to other Skype users. But using VoIP can sometimes be a frustrating experience. So, use these hacks to solve some common VoIP woes. 5.11.1. Troubleshoot VoIP Phone/Home Router Problems Some people have had problems when using Vonage VoIP service with their home routers. Instead of incoming calls being sent to their phones, the calls go directly to voicemail. How you solve this varies from router to router, but here's how to do it with the popular Linksys router line. Other routers should have similar fixes. You're going to set up your router so that it uses its port forwarding feature to send calls directly to your IP telephone. First, turn off your cable modem or DSL modem, all the computers on your network, your router, and your IP telephone. Then, turn your cable modem or DSL modem and your router back on. Turn on your IP telephone, and make sure that turn it on before turning on any PCs on your network. This will make sure it is given the network's first IP address via DHCP.
|
|
 Forwarding. You'll come to the port forwarding screen. Set up port forwarding to route these port ranges to your IP telephone. Forward each port to the IP address of your IP phone, such as 192.168.1.101. (The IP address will be the first one assigned by your network.) Set the protocol to UDP. Use the port settings in Table 5-8. Table 5-8. Port ranges for your IP telephone Port range Protocol IP address
Forwarding. You'll come to the port forwarding screen. Set up port forwarding to route these port ranges to your IP telephone. Forward each port to the IP address of your IP phone, such as 192.168.1.101. (The IP address will be the first one assigned by your network.) Set the protocol to UDP. Use the port settings in Table 5-8. Table 5-8. Port ranges for your IP telephone Port range Protocol IP address| 53 to 53 | UDP | Your phone's IP address |
| 5060 to 5061 | UDP | Your phone's IP address |
| 123 to 123 | UDP | Your phone's IP address |
| 69 to 69 | UDP | Your phone's IP address |
| 10000 to 20000 | UDP | Your phone's IP address |
Your screen will look like Figure 5-6. Figure 5-6. Setting up a Linksys router to work with a Vonage IP phone

|
When you're done, click Apply. The port forwarding will take effect immediately, so your problems should be solved. 5.11.2. Get Your Vonage IP Phone to Work with DSL The nature of some DSL services cause conflicts with Vonage IP telephones, so when you use DSL, you might not be able to get your IP phone to work. Even if the phone previously worked with a cable modem, when you switch to DSL it might stop working. The problem is that DSL services often require the use of PPPoE, but if you don't also turn on PPoE in your Vonage phone, the phone won't work. To turn on PPPoE in your Vonage phone, open a web browser in the computer that has the phone connected to it. Go to http://192.168.102.1 and press Enter. (That's the default address for configuring Vonage phones. If you have another type of phone, or if your Vonage phone has a different configuration address, use that instead.) The phone's Basic Configuration screen will appear. Select the Enable PPPoE option, and type the DSL service name, username, and password that your DSL provider gave to you. Click Save Changes. You'll get the message "This will require a reboot of the unit. Are you sure?" Click OK. Your phone will reboot. Wait five minutes, and pick up your phone. It will now work.
Is VoIP a Telephone or Internet Service?When you use VoIP, are you making a phone call or using the Internet? The logical answer, of course, is both. But state and federal governments are not logical, so that question makes an enormous difference in how VoIP services will be regulated. If VoIP is treated as if it were a telephone service, for example, VoIP companies could be required to provide Enhanced 911 emergency phone services and pay into federal and state universal service funds that are used to help pay for telecommunications service to low-income areas, schools, and libraries. Also unclear is whether VoIP services must comply with federal wiretap laws. At the time of this writing, the Federal Communications Commission hasn't made a definitive decision on the matter, but it has made a series of rulings related to VoIP. It ruled that software-only VoIP that makes PC-to-PC phone calls only is not a phone service and therefore does not have to comply with phone service regulation. It also ruled that state governments do not have regulatory authority over VoIP services that use the telephone system to let you make and receive phone calls to anyone, anywhere, as a phone service. Instead, the federal government has that authority. But as of this writing, it still hasn't ruled on whether it will treat that service like a telephone call, like Internet access, like some hybrid of the two, or in some other way. |
5.11.3. Cut Your DSL Costs with VoIP Many DSL services let you make phone calls as well as get high-speed Internet access over the same telephone line. So, if you use VoIP in concert with DSL, you're paying double for your phone serviceonce for DSL, and the second time for VoIP. There's a solution: get a DSL service that offers only Internet access, not phone service. It's sometimes called Naked DSL. Qwest and Verizon both offer Naked DSL, and other DSL providers might follow suit.
|
5.11.4. Make Skype Calls at Work If you try to make Skype calls at work, you might get a "Skype error #1102" and be unable to make a connection. If that happens, it means your business's firewall won't let you through. To make the calls, you'll have to tell the system administrator to open up unrestricted outgoing TCP access to all destination ports above 1024, or to port 80. (Destination ports above 1024 is a better bet, however.) That will let you make the connection. If you want better voice quality, tell the administrator to also open up outgoing UDP traffic to all ports above 1024, and to allow UDP replies to come back in.
Tweak DNS Settings for Faster Internet Acces
Each entry in the file should be on one line. The IP address should be in the first column, and the corresponding hostname in the next column. At least one space should separate the two columns. You can add comments to the file by preceding the line with a #, in which case the entire line will be ignored by the file, or by putting a # after the hostname, in which case only the comment after will be ignored. You might want to comment on individual entriesfor example:130.94.155.164 gralla.com #still in beta
When you're finished editing the file, save it to its existing location.
|
5.2.2. Adjust XP's DNS Cache Settings As a way of speeding up DNS, when you visit a site XP puts the DNS information into a local DNS cache on your PC. So, when you want to go to a site, XP first looks in its local DNS cache, called the resolve cache, to see whether the DNS information is contained there. That way, if it finds the information locally, it doesn't have to query a remote DNS server to find IP information. The cache is made up of recently queried names and entries taken from your HOSTS file. The cache contains both negative and positive entries. Positive entries are those in which the DNS lookup succeeded, and you were able to connect to the web site. When XP looks in the cache, if it finds a positive entry it immediately uses that DNS information and sends you to the requested web site. Negative entries are those in which no match was found, and you end up getting a "Cannot find server or DNS" error in your browser. Similarly, when XP looks in the cache and finds a negative entry, it gives you the error message without bothering to go out to the site. Negative entries can lead to problems. When you try to make a connection to a site that has a negative entry in your cache, you'll get an error message, even if the site's problems have been resolved and it's now reachable. You can solve this problem, though, using a Registry hack. By default, XP caches negative entries for five minutes. After five minutes, they're cleared from your cache. But if you'd like, you can force XP not to cache these negative entries so that you'll never run into this problem. Run the Registry Editor [Hack #83] and go to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters. Create a new DWORD value with the name NegativeCacheTime and give it a value of 0. (The value might already exist. If it does, edit its value to 0.) The DWORD determines how much time, in seconds, to keep negative entries in the DNS cache. If you like, you can have the entries stay alive for one second by giving the DWORD a value of 1. After you're done editing, exit the Registry. To make the change take effect, restart your computer, or flush your cache by issuing the command ipconfig /flushdns at a command prompt.
|
That command will flush your DNS cacheall the entries, both positive and negative, will be flushed, and it will be empty until you start visiting web sites. Negative entries, however, will not be added to the cache if you've given the DWORD a value of 0. You can also use the Registry to control the amount of time positive entries are kept in the DNS cache. By default, they are kept for 24 hours. To change the default, go to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters again and create a DWORD value called MaxCacheEntryTtlLimit. (If it's already present, just edit the value.) For the value, enter the amount of time you want the entry to remain, in seconds, making sure to use Decimal as the base. 5.2.3. Fix DNS Problems Sometimes, when you can't connect to a web site, the cause is a DNS problem. There are things you can do to solve these problems, though. If you're having trouble connecting to a site, to find out if DNS is a potential culprit first ping [Hack #51] the site to which you can't connect by issuing the ping command at the command prompt or in the Run box, like this:ping www.zdnet.com
If the site is live, you'll get an answer like this:Pinging www.zdnet.com [206.16.6.252] with 32 bytes of data: Reply from 206.16.6.252: bytes=32 time=119ms TTL=242 Reply from 206.16.6.252: bytes=32 time=79ms TTL=242 Reply from 206.16.6.252: bytes=32 time=80ms TTL=242 Reply from 206.16.6.252: bytes=32 time=101ms TTL=242 Ping statistics for 206.16.6.252: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 79ms, Maximum = 119ms, Average = 94ms
If it's not, you'll get a response like this:Ping request could not find host. Please check the name and try again.
If you ping a site and it's live, but you can't connect to it with your browser, a DNS problem might be the reason. If you suspect you're having a DNS problem, take the following actions:
- Check your HOSTS file
- Check your DNS settings
 Details, and look at the bottom of the tab to find your DNS servers. If they don't match what they're supposed to be, right-click the problem connection and choose Properties. Then, highlight Internet Protocol (TCP/IP) and choose Properties. Change the DNS servers to the proper ones, or choose "Obtain DNS server address automatically" if your ISP or network administrator tells you to.
Details, and look at the bottom of the tab to find your DNS servers. If they don't match what they're supposed to be, right-click the problem connection and choose Properties. Then, highlight Internet Protocol (TCP/IP) and choose Properties. Change the DNS servers to the proper ones, or choose "Obtain DNS server address automatically" if your ISP or network administrator tells you to. - Flush your DNS cache
- Find out if your ISP is having DNS problems
Troubleshoot Network Connections with ping, tracert, and pathping
where target is either a hostname or an IP addressfor example, pop3.catalog.com, zdnet.com, or 209.217.46.121. In response, you'll get information in this format:Pinging zdnet.com [206.16.6.208] with 32 bytes of data: Reply from 206.16.6.208: bytes=32 time=83ms TTL=242 Reply from 206.16.6.208: bytes=32 time=73ms TTL=242 Reply from 206.16.6.208: bytes=32 time=91ms TTL=242 Reply from 206.16.6.208: bytes=32 time=72ms TTL=242 Ping statistics for 206.16.6.208: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 72ms, Maximum = 91ms, Average = 79ms
If the host isn't active, instead of getting this report you'll get the message "Request timed out." If you enter a hostname, ping reports back with its IP address and then gives details about its four attempts to contact the host, a measurement of how long (in milliseconds) the packet took to make the round trip between your PC and the host, the Time To Live (TTL) information about each packet, and a summary of its findings. The TTL field can tell you how many hops the packets took to get from your PC to its destination. TTL initially specified the amount of time a packet could live, in seconds, before it expired, as a way to make sure packets didn't simply bounce around the Internet forever and create traffic jams. However, it has been reinterpreted to mean the maximum number of hops a packet will be allowed to take before it reaches its destination. The default number is 255. Each time a packet takes another hop, its TTL is reduced by one. The TTL number that ping reports is the packet's final TTL when it reaches its destination. To find out the number of hops a packet takes, subtract its initial TTL (by default, 255) from the TTL reported by ping. In our example, the packets took 13 hops to get to their destination. You can use ping with switches, like so:ping -a -l 45 208.201.239.237
This command changes the packet size sent from its default size of 32 bytes to 45 bytes, and resolves the IP address to a hostnamein other words, it lists the IP address's hostname. ping has a wide variety of useful switches that you can use for all kinds of troubleshooting. You use the basic ping command to check whether an Internet or network resource is live and to see if there are any delays in reaching it. But, as Table 5-2 shows, you can use ping and its switches for many other purposes as wellfor example, to find out the IP address of a hostname, and vice versa. Table 5-2. Useful ping switches Switch What it does
-a Resolves an IP address to a hostname.
-f Turns on the Don't Fragment flag for a packet. This lets you send packets that don't get broken up, and it can be useful for when you want to test whether packets of a certain size are getting through.
-i value Sets the value of the TTL field, using a number from 0 to 255. When you use this field, even though the field will be set to the number you specify, note that the ping report will report back as if it were set to 255. For example, if you set a TTL of 20 and the packet takes 15 hops, the TTL value ping reports will be 240.
-l value Pings using the value specified, in number of bytes.
-n count Specifies the number of ICMP Echo Request messages sent, instead of the default number of 4.
-r count Displays the IP addresses of the hops taken along the route to the destination. Specify a number between 1 and 9. If the number of actual hops exceeds the number you specify, you will get a "Request timed out" message.
-s count Displays a timestamp for the Echo Request and the Echo Reply Request for hops along the route. Specify a number between 1 and 4. If the number of actual hops exceeds the number you specify, you will get a "Request timed out" message.
-t Keeps sending the Echo Request message continually until stopped by pressing Ctrl-Break, Pause, or Ctrl-C.
-w value The maximum amount of time (in milliseconds) to wait for an Echo Reply message for each Echo Request message before issuing a timeout message. The default is 4000 (4 seconds).
5.4.2. Trace Your Network and Internet Data Path with tracert Frequently, you have a connection problem over your network or the Internet not because your final destination is down, but because there's a problem with a router somewhere between you and your final destination. For troubleshooting those kinds of problems, use tracert. It displays the path that data takes en route to the server or service you're trying to reach, either on your network or across the Internet. As with ping, it does this by sending ICMP Echo Request messages to the destination you're checking on. To use it, type TRacert destination at a command prompt, where destination can be either an IP address or a hostname. Following is a typical response from a tracert command:Tracing route to redir-zdnet.zdnet.com [206.16.6.208] over a maximum of 30 hops: 1 9 ms 11 ms 10 ms 10.208.128.1 2 8 ms 8 ms 7 ms bar02-p0-1.cmbrhe1.ma.attbb.net [24.128.8.53] 3 9 ms * 32 ms bar03-p7-0.wobnhe1.ma.attbb.net [24.147.0.193] 4 8 ms 14 ms 9 ms 12.125.39.213 5 12 ms 10 ms 9 ms gbr2-p70.cb1ma.ip.att.net [12.123.40.102] 6 25 ms 26 ms 24 ms gbr4-p80.cb1ma.ip.att.net [12.122.5.65] 7 36 ms 39 ms 64 ms gbr4-p40.cgcil.ip.att.net [12.122.2.49] 8 33 ms 33 ms 48 ms gbr3-p60.cgcil.ip.att.net [12.122.1.125] 9 72 ms 80 ms 78 ms gbr3-p30.sffca.ip.att.net [12.122.2.150] 10 72 ms 77 ms 73 ms idf26-gsr12-1-pos-6-0.rwc1.attens.net [12.122.255.222] 11 76 ms 78 ms 79 ms mdf3-bi4k-2-eth-1-1.rwc1.attens.net [216.148.209.66] 12 73 ms 72 ms 74 ms 63.241.72.150 13 72 ms 74 ms 71 ms redir-zdnet.zdnet.com [206.16.6.208]
If the destination can't be reached, you will get the message "Destination unreachable." As you can see, tracert shows the IP address and hostname address of each hop, along with timing data for each hop. If you're having problems on your network, this can help you locate the source of the problem; if a hop has a particularly long delay, you know that's the cause. You can use several switches with tracert, like this:Tracert -d -h 45 zdnet.com
This command traces to zdnet.com, displaying only the IP addresses of each router and specifying a maximum number of 45 hops en route to the destination. Table 5-3 shows the most useful tracert switches. Table 5-3. Useful tracert switches Switch What it does
-d Does not display the hostname of each router
-h value Sets a maximum number of hops for the trace to the destination
-w value Sets the maximum amount of time in milliseconds to wait for a reply
5.4.3. Troubleshoot Network Problems with pathping The pathping command works like a combination of ping and tracert. Type pathping from the command line, like this:pathping target
where target is either a hostname or an IP addresspop3.catalog.com or 209.217.46.121, for example. You then get a two-part report: first a list of every hop along the route to the destination, and then statistics about each hop, including the number of packets lost at each hop. It uses switchesfor example:pathping -n -w 1000 oreilly.com
This command tells pathping not to resolve the IP addresses of routers, and to wait one second (1,000 milliseconds) for an Echo Reply message. Table 5-4 lists the most important pathping switches. Table 5-4. Useful pathping switches Switch What it does
-n Does not display the hostname of each router.
-h value Sets a maximum number of hops for the trace to the destination. The default is 30 hops.
-w value Sets the maximum amount of time (in milliseconds) to wait for a reply.
-p Sets the amount of time (in milliseconds) to wait before a new ping is issued. The default is 250.
-q value Sets the number of ICMP Echo Request messages to transmit. The default is 100.
close Welcome! Wikis are websites that everyone can build together. It's easy! Troubleshoot Network Connections with netsh, netstat, and ipconfig
| connect ieproxy | Establishes a connection to Internet Explorer's proxy server, if one exists |
| connect mail | Establishes a connection to the default Outlook Express mail server |
| connect news | Establishes a connection to the default Outlook Express newsgroup server |
| ping adapter | Establishes a connection with the named adapter |
| ping dhcp | Establishes a connection with a DHCP server |
| show adapter | Lists all the adapters on the PC |
| show all | Lists all the network objects defined for the local PC, such as adapters, network clients, servers, modems, and other objects |
| show dhcp | Lists all the DHCP servers for the specified adapter |
| show dns | Lists all the DNS servers for the specified adapter |
| show gateway | Lists all the gateways for the specified adapter |
5.5.2. Use netstat to Get Information About Open Network Connections If you want to get a snapshot of all incoming and outgoing network connections, use the netstat command. At a command prompt, type netstat. It lists all connections, including the protocol being used, the local and Internet addresses, and the current state of the connection, like this:Active Connections Proto Local Address Foreign Address State TCP PrestonGralla:1031 localhost:2929 ESTABLISHED TCP PrestonGralla:2887 192.168.1.103:netbios-ssn TIME_WAIT TCP PrestonGralla:2899 www.oreillynet.com:http ESTABLISHED TCP PrestonGralla:2900 www.oreillynet.com:http ESTABLISHED TCP PrestonGralla:2932 mail.attbi.com:pop3 ESTABLISHED TCP PrestonGralla:2936 vmms2.verisignmail.com:pop3 ESTABLISHED
It will help you know whether connections are live, the network or Internet device to which they're connected, and which local resource is making the connection. It's best suited for when you're troubleshooting network problems and want to find out whether certain ports are open, why certain computers on the network are having connection problems, and similar issues. You can use command-line switches with netstat. For example, display open ports and open connections with this syntax: netstat -a. Table 5-6 lists netstat switches. Table 5-6. Useful netstat switches Switch What it does
| -a | Displays all open connections and ports. |
| -e | Displays Ethernet statistics about packets transmitted and received. Can be combined with the -s switch. |
| -n | Displays the addresses and ports in numeric, IP address form. |
| -o | Displays the process identifier (PID) that owns each connection. |
| -p proto | Displays the connections used by the protocol, which can be IP, IPv6, ICMP, ICMPv6, TCP, TCPv6, UDP, or UDPv6. |
| -r | Displays the network's routing table. |
| -s | Displays statistics for each protocol. It lists all statistics for all protocols, but you can list only those for a specified protocol if you combine it with the -p switch. |
| interval value | Runs netstat repeatedly, pausing value seconds between each new display. To stop the display, press Ctrl-C. |
5.5.3. Use ipconfig to Troubleshoot TCP/IP One of the most powerful tools for analyzing and troubleshooting TCP/IP problems is the ipconfig command-line utility. It provides information about each of your adapters, including the assigned IP address, subnet mask, default gateway, MAC address, DNS servers, whether DHCP is enabled, and a variety of other data. To see basic information about your adapters, type ipconfig at a command prompt, and you'll see information like this:Windows IP Configuration Ethernet adapter Local Area Connection: Connection-specific DNS Suffix . : ne1.client2.attbi.com IP Address. . . . . . . . . . . . : 192.168.1.100 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 192.168.1.1 PPP adapter {6A724E76-AB59-4ABC-BBF5-41CA4410EB8D}: Connection-specific DNS Suffix . : IP Address. . . . . . . . . . . . : 172.165.155.106 Subnet Mask . . . . . . . . . . . : 255.255.255.255 Default Gateway . . . . . . . . . :
As you can see, ipconfig provides basic information about your IP address, subnet mask, default gateway, and a connection-specific DNS suffix, if any. However, you can get much more detailed information by using the /all switch, like this: ipconfig /all. For most troubleshooting purposes, use the /all switch. You get a much more comprehensive listing, as shown here:Windows IP Configuration Host Name . . . . . . . . . . . . : PrestonGralla Primary Dns Suffix . . . . . . . : Node Type . . . . . . . . . . . . : Hybrid IP Routing Enabled. . . . . . . . : No WINS Proxy Enabled. . . . . . . . : No Ethernet adapter Local Area Connection: Connection-specific DNS Suffix . : ne1.client2.attbi.com Description . . . . . . . . . . . : CNet PRO200WL PCI Fast Ethernet Adapter Physical Address. . . . . . . . . : 00-08-A1-00-9F-32 Dhcp Enabled. . . . . . . . . . . : Yes Autoconfiguration Enabled . . . . : Yes IP Address. . . . . . . . . . . . : 192.168.1.100 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 192.168.1.1 DHCP Server . . . . . . . . . . . : 192.168.1.1 DNS Servers . . . . . . . . . . . : 204.127.202.19 216.148.227.79 Lease Obtained. . . . . . . . . . : Saturday, December 28, 2002 8:53:40 AM Lease Expires . . . . . . . . . . : Sunday, December 29, 2002 8:53:40 AM PPP adapter {6A724E76-AB59-4ABC-BBF5-41CA4410EB8D}: Connection-specific DNS Suffix . : Description . . . . . . . . . . . : WAN (PPP/SLIP) Interface Physical Address. . . . . . . . . : 00-53-45-00-00-00 Dhcp Enabled. . . . . . . . . . . : No IP Address. . . . . . . . . . . . : 172.165.155.106 Subnet Mask . . . . . . . . . . . : 255.255.255.255 Default Gateway . . . . . . . . . : DNS Servers . . . . . . . . . . . : 64.12.104.134 NetBIOS over Tcpip. . . . . . . . : Disabled
You can also use ipconfig to release and renew IP addresses, and to perform other troubleshooting functions as well. For example, to renew an adapter's IP address, use this command:ipconfig /renew "adapter name"
where adapter name is the name of the adapter whose IP address you want to renew. Make sure to put quotes around the adapter name and use spaces if there is more than one word in the adapter name. Table 5-7 lists other switches you can use with ipconfig. Table 5-7. Command-line switches for ipconfig Switch What it does
| /all | Displays complete TCP/IP configuration information |
| /displaydns | Displays information from the DNS resolver cache [Hack #49] |
| /flushdns | Clears the DNS resolver cache [Hack #49] |
| /registerdns | Refreshes all DHCP leases and reregisters DNS names |
| /release "adapter" | Releases the IP address for the specified adapter |
| /renew "adapter" | Renews the IP address for the specified adapter |
| /setclassid "adapter" newclassid | Resets the DHCP Class ID for the specified adapter |
| /showclassid "adapter" | Displays the DHCP Class ID for the specified adapter |
Speed Up Network Browsing
|
This unnecessary checking can easily add 30 seconds of delay. You can decrease the time browsing takes by modifying the Registry to turn off this checking:
- Invoke the Registry Editor by typing regedit [Hack #83] at the command line.
- Open the following Registry key:HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ Remote Computer\NameSpace
- Delete the following key (the value for it is the Scheduled Tasks, as shown in Figure 5-4):{D6277990-4C6A-11CF-8D87-00AA0060F5BF}
- Close the Registry and reboot.

That's it! You should now be able to browse to another computer on the network without much delay.
Repair a Broken TCP/IP Connection
- Try automated repair
- Run the Network Setup Wizard
- Reset your router
- Reset your cable modem or DSL modem
- Reset TCP/IP to its original configuration
- Get a new Ethernet cable
Renew Your DHCP-Assigned IP Address

Optimize Your Home Router
Connect on Demand and Maximum Idle Time settings Depending on your ISP, you might become disconnected from the Net after you haven't used the Internet for a certain amount of time. To solve the problem, if your router has a Connect on Demand setting, enable it; that will automatically reestablish your Internet connection when you use an Internet service, even if your ISP has cut you off. If there is a Maximum Idle Time setting, set it to 0 so that your router will always maintain an Internet connection, no matter how long you haven't used the Internet. As a practical matter, you should need to use only one of these two settings; either one will maintain a constant Internet connection for you.
Keep Alive setting Use this setting to maintain a constant Internet connection, even if your PC is idle. It's similar to the Connect on Demand and Maximum Idle Time settings, except that it doesn't let your connection disconnect, so it is an even better setting to enable, if your router has it.
Router Password Your router requires a password for you to use its administrator account. It comes with a default password. For example, Linksys routers come with a default password of admin. Change the password for maximum security.
Enable Logging For security reasons, it's a good idea to enable logging so that you can view logs of all outgoing and incoming traffic. Depending on your router, it might save permanent logs to your hard disk or allow only the viewing of temporary logs. You might also be able to download extra software from the manufacturer to help keep logs. For example, Linksys routers use temporary logs, but if you want to save permanent logs, you can download the Linksys Logviewer software from http://www.linksys.com. You can view logs using a text editor, like Notepad, or a log analysis program, such as the free AWStats (http://awstats.sourceforge.net). 5.3.1. Special Hub/Router Settings for DSL Access If you have DSL access, you might need to customize your router's settings to provide your network with Internet access; sometimes the router's settings block Internet access. Here are the settings you'll need to change so that you can get onto the Internet:
PPPoE (Point to Point Protocol over Ethernet) Some DSL ISPs use this protocol when offering Internet access. By default, this protocol is disabled on routers because it's normally not required for Internet access. However, if you have DSL access, you might need to enable it in your router.
Keep Alive setting Some DSL ISPs will automatically disconnect your connection if you haven't used it for a certain amount of time. If your router has a Keep Alive setting, enable it by clicking the radio button next to it; this will ensure that you are never disconnected.
MTU (Maximum Transmission Unit) As a general rule, DSL users should use a value of 1492 for their MTU. The MTU sets the maximum size of packets a network can transmit. Any packets larger than the MTU setting will be broken into smaller packets. DSL ISPs often set the MTU to 1492, so if you set a packet size larger or smaller than that, you might slow down Internet access.
|
5.3.2. Settings for Using a VPN If you use a Virtual Private Network (VPN) [Hack #82] to connect to your corporate network from home and you use a router, you might run into difficulties and not be able to connect to the VPN. Some routers, such as those from Linksys, are specifically designed to work with VPNs and have specific setup screens for them; if you have one of those, you shouldn't have any problems. Make sure to get the proper encryption, authentication, and similar information about the VPN from your network administrator, and then use those settings for the VPN setup screen in your router. However, you might run into problems running a VPN with a router that doesn't have specific VPN settings, even if the device claims it will work with VPNs. In particular, one default setting, hidden fairly deeply in most router setup screens, can disable VPN access; some routers, such as those made by Linksys, include an option called Block WAN Request. By default, this option is enabled and blocks requests into the network from the Internet; for example, it stops ping requests into the network. However, enabling this option also blocks VPN access. VPN access requires that requests get into the network from the Internet, so if you block those requests the VPN won't work. If you have a Linksys router, disable this setting by logging into your administrator's screen, choosing Advanced
 Filters, selecting Disable Block WAN Request, and clicking Apply. For other routers, check the documentation. VPNs use a variety of protocols for tunneling through the Internet, such as IPSec and the Point-to-Point Tunneling Protocol (PPTP). Make sure these settings are enabled on your router if you want to use it in concert with a VPN. 5.3.3. Enable Specific Internet Services: Port Forwarding Residential routers often use Network Address Translation (NAT), in which the router's single, external IP address is shared among all the computers on the network, but each computer has its own internal IP address, invisible to the Internet. For example, to the Internet each computer looks as if it has the address of 66.32.43.98, but internally they have different addresses, such as 192.168.1.100, 192.168.1.101, and so on. The routers have built-in Dynamic Host Configuration Protocol (DHCP) servers that assign the internal IP address. These internal IP addresses allow the PCs to communicate with each other and to connect to the Internet, and they also offer protection to PCs on the network. To the rest of the Internet, each PC has the IP address of the router, so each PC's resources can't be attacked or hijackedthey're invisible. The router itself doesn't have resources that can be used to attack your PCs, so you're safe. But if you have servers on your network that need to provide Internet-related services (perhaps you have an FTP or web server), or if you need to allow certain PCs to be connected to the Internet for specific purposes (such as for playing multiplayer games), you'll run into trouble because they don't have IP addresses that can be seen by the rest of the Internet. However, with this trick, you can use your router to forward incoming requests to the right device on your network. For example, if you have a web server, FTP server, or mail server and you want people to be able to connect to them, you'll be able to route incoming requests directly to those servers. PCs on the Internet will use your router's IP address, and your router will then route the requests to the proper device on your network. Normally, the devices would not be able to be connected to because the IP addresses they are assigned by the router are internal LAN addresses, unreachable from the Internet. Not all routers include this capability.To use this feature in a Linksys router, log into your administrator's screen and choose Advanced
Filters, selecting Disable Block WAN Request, and clicking Apply. For other routers, check the documentation. VPNs use a variety of protocols for tunneling through the Internet, such as IPSec and the Point-to-Point Tunneling Protocol (PPTP). Make sure these settings are enabled on your router if you want to use it in concert with a VPN. 5.3.3. Enable Specific Internet Services: Port Forwarding Residential routers often use Network Address Translation (NAT), in which the router's single, external IP address is shared among all the computers on the network, but each computer has its own internal IP address, invisible to the Internet. For example, to the Internet each computer looks as if it has the address of 66.32.43.98, but internally they have different addresses, such as 192.168.1.100, 192.168.1.101, and so on. The routers have built-in Dynamic Host Configuration Protocol (DHCP) servers that assign the internal IP address. These internal IP addresses allow the PCs to communicate with each other and to connect to the Internet, and they also offer protection to PCs on the network. To the rest of the Internet, each PC has the IP address of the router, so each PC's resources can't be attacked or hijackedthey're invisible. The router itself doesn't have resources that can be used to attack your PCs, so you're safe. But if you have servers on your network that need to provide Internet-related services (perhaps you have an FTP or web server), or if you need to allow certain PCs to be connected to the Internet for specific purposes (such as for playing multiplayer games), you'll run into trouble because they don't have IP addresses that can be seen by the rest of the Internet. However, with this trick, you can use your router to forward incoming requests to the right device on your network. For example, if you have a web server, FTP server, or mail server and you want people to be able to connect to them, you'll be able to route incoming requests directly to those servers. PCs on the Internet will use your router's IP address, and your router will then route the requests to the proper device on your network. Normally, the devices would not be able to be connected to because the IP addresses they are assigned by the router are internal LAN addresses, unreachable from the Internet. Not all routers include this capability.To use this feature in a Linksys router, log into your administrator's screen and choose Advanced  Forwarding to get to the screen shown in Figure 5-1. Figure 5-1. Forwarding incoming requests to the proper server or device
Forwarding to get to the screen shown in Figure 5-1. Figure 5-1. Forwarding incoming requests to the proper server or device
When this feature is enabled, the router examines incoming requests, sees what port they're directed to (for example, port 80 for HTTP), and then routes the request to the proper device. Fill in each device's IP address, the protocol used to connect to it, and the port or port range you want forwarded to it. It's also a good idea to disable DHCP on each device to which you want to forward requests and instead give them static internal IP addresses. If you continue to use DHCP instead of assigning them a static IP address, the IP addresses of the servers or devices might change and would therefore become unreachable. Check your router's documentation on how to force it to assign static IP addresses to specific devices. Table 5-1 lists port addresses for common Internet services. For a complete list of ports, go to http://www.iana.org/assignments/port-numbers. Table 5-1. Common Internet TCP ports Port number Service
| 7 | Echo |
| 21 | FTP |
| 22 | PCAnywhere |
| 23 | Telnet |
| 25 | SMTP |
| 42 | Nameserv, WINS |
| 43 | Whois, nickname |
| 53 | DNS |
| 70 | Gopher |
| 79 | Finger |
| 80 | HTTP |
| 81 | Kerberos |
| 101 | HOSTNAME |
| 110 | POP3 |
| 119 | NNTP |
| 143 | IMAP |
| 161 | SNMP |
| 162 | SNMP trap |
| 1352 | Lotus Notes |
| 3389 | XP's Remote Desktop |
| 5010 | Yahoo! Messenger |
| 5190 | America Online Instant Messenger (AIM) |
| 5631 | PCAnywhere data |
| 5632 | PCAnywhere |
| 7648 | CU-SeeMe |
| 7649 | CU-SeeMe |
5.3.4. Cloning a MAC Address for Your Router There once was a time when cable companies banned home networks, or when they charged extra when you ran one at home. The theory was that because you were using so much extra bandwidth for multiple computers, you should be charged extra. Thankfully, those days are goneor at least they should be. If you're one of the unlucky few who has a cable or DSL company that charges extra for a home network, there's something you can do to get around the problem. This hack will help with that, and it will help if you have a cable or DSL provider that requires that you provide the Media Access Control (MAC) address of your network adapter for your connection to work. If you had a single PC when you began your broadband service, but you've since installed a router at home to set up a network and share Internet access among several PCs, you'll have to provide the ISP with your new router's MAC address. There is a way to use your existing MAC address with your new router by cloning the address. To your ISP, it looks as if your MAC address hasn't changed. You might want to do this even if your cable provider doesn't charge extra for several PCs because it will save you from having to call up the cable company's tech-support line to provide a new MAC address. Note that not all routers have this capability, so yours might not be able to do it. Most Linksys routers let you do this, so if you have a Linksys, do the following to clone your MAC address. Depending on your model, the exact steps might vary:
- Find out your current network adapter's MAC address (the MAC address your broadband provider already has) by opening a command prompt, typing ipconfig /all, and looking under the entry for "Ethernet adapter Local Area Connection." You'll see an entry like this:Physical Address. . . . . . . . . : 00-08-A1-00-9F-32
- That's your MAC address.
- Log into your administrator's screen for the Linksys router and choose Advanced
MAC Addr. Clone. A screen similar to Figure 5-2 appears. Figure 5-2. Cloning an existing MAC address

- Type in the name of the MAC address you've obtained from your network adapter and click Apply. Your router will now be recognized by your ISP. Note that you might have to power down your cable modem and then power it back up for the router to be recognized.
|
5.3.5. Manage Your Network's Bandwidth There's one problem with home networks that share a single Internet connection: one PC can hog all the bandwidth. For example, if someone in your house uses file-sharing software, that can suck up just about all of a network's spare bandwidth, and everyone else who's connected might see their connections slow to a crawl. There's a simple answer for the problem. Use software that will limit the bandwidth that any single PC on your network can use. So, if you have a 3-megabit-per-second connection, you could limit any PCs to .5 megabits per second, for example. That way, anyone can still share files with others at a reasonable rate, but still let others get high-speed connections. NetLimiter (http://www.netlimiter.com), shown in action in Figure 5-3, is a great program for doing this. Figure 5-3. Setting bandwidth limits on a PC-by-PC basis on your network with NetLimiter

Not only will you be able to set bandwidth limits per PC, but you'll also be able set upload and download transfer rates for individual programs on a PC. So, you could give more of an individual PC's bandwidth to file sharing, for example, and less to email. NetLimiter is shareware; you can try it out for free, but after 28 days, you're expected to pay $29.95 to the developer.

